SPF DKIM and DMARC Explained With ISP Support
Published on 2020-05-23· Updated on 2024-01-25
SPF, DKIM, and DMARC are the three main email security protocols that complement one another. They are methods to authenticate a mail server and help prove to Internet Service Providers (ISPs), mail services, and other mail servers that senders are truly authorized to send an email.
This is done to prevent someone else from sending emails on behalf of you by using your domain address.
Moreover, authenticating your account with these methods will establish you as a legitimate sender in the view of the receiving server. You can readily configure and adjust these parameters within the domain control panel by adding TXT records to the domain's DNS settings.
SPF (Sender Policy Framework): SPF authentication works by specifying the number of allowed IPs that can send emails from your domain. When configuring SPF, the domain owner can specify the allowed sending domains by adding a record on the server.
SPF helps in verifying the authenticity of the sender's domain, and this, in turn, can influence the recipient's decision to open an email. SPF primarily serves to strengthen the Domain Name System (DNS) server, which translates web addresses into IP addresses, enabling internet connections. Without proper DNS configuration, websites may not be accessible.
Additionally, SPF plays a crucial role in preventing domain spoofing. It helps in verifying that the email sender is authorized to use a particular domain's name in the "From" address of an email. This validation helps reduce the likelihood of email-based scams and phishing attacks, as recipients can trust the source of the email, making SPF an important component of email security.
SPF consists of three primary components:
- Policy Framework: This element defines the rules and policies for verifying the authenticity of email senders. It outlines what actions should be taken when an email doesn't comply with the SPF policy.
- Authentication Method: SPF relies on specific authentication methods to determine if the sender's domain is authorized to send emails on behalf of that domain. This method is used to authenticate the sender's identity.
- Specialized Headers: SPF often involves adding specialized headers to email messages. These headers can contain information related to SPF checks and results, helping the recipient's email system make informed decisions about whether to accept or reject the email based on SPF policies.
DKIM (DomainKeys Identified Mail): DKIM authentication is similar to SPF. The DKIM is added as a TXT record by adding it in your domain panel. It ensures none of the emails going from one server to another is tampered with by anyone in the middle, and it can be clearly identified by the other end.
DMARC(Domain-based Message Authentication): Domain-based Message Authentication, Reporting, and Conformance (DMARC) is also referred to as ‘email signing.’ It ties the first two email security protocols (the SPF and DKIM) together with a more consistent set of policies.
DMARC builds on SPF and DKIM to validate emails further by matching the validity of these records. This enables you to set policies and generate reports in case the DMARC validation fails.
DMARC has three basic purposes:
- To verify that the sender’s email message is protected by both DKIM and SPF protocols.
- To inform the receiving mail server what it should do if neither of those email security protocols passes and
- To provide a way for the receiver server to report to the sender about the email message that failed or passed the DMARC evaluation.
FAQ
- Difference between the working
- ISP Wise Support for Email Authentication
- ISP Recommendations for Email Authentication
Difference between the working of authentication mechanisms
Working on each of these authentication mechanisms differs according to the objective they are trying to achieve. Let us see how they differ.
SPF
Installation: The txt record in domain DNS needs to be set; this record will contain a bunch of valid server IPs that can send emails through the specific domain.
Structure:
v=spf1 include:54443444.domain.net ~all
Each email you send contains a return path header that specifies the email address for delivery notifications, particularly concerning email bounces and spam. To enhance email security, SPF plays a crucial role. Here's how it works:
- Extracting the sending server's domain: When an email is sent, the domain path of the sending server is extracted.
- Fetching DNS record details: The DNS records of the sending server's domain are retrieved.
- Adding SPF credentials: SPF credentials are added to the domain's TXT record. This record contains a list of authorized IP addresses that are allowed to send emails on behalf of the domain.
- SPF validation: During the SPF validation process, the recipient's email server checks if the IP address of the received email server is listed in the SPF record. If it is, the email is considered validated. If not, it is up to the recipient's email service to determine how to handle the email.
DKIM:
Installation: Generate a public key and ensure that you specify the corresponding private key. Set the hash of the public key in the TXT record. Enable email signing to initiate the process of sending email signatures.
Structure:
DKIM Set in txt record with the public key
k=rsa; p=MIGfMA0GCksjlkdixcieJDDSFIELDSKFLCBiQKBgQDLMMExLiGRqzJkNdNIjUnLX7JL0wjbwwENDoXgJIBisIsrofLPetZM401dioNU8k//Yw5/iyzhyrWsIyINyyHs77EoDFDDEEFFEKJKLJHLKifLN51IIvwIDAQABQp6nIyi5oioyZh+1jDXoCDDFDSFEEDSFSEFE85N7b76aTtHmy2wTgR2LFS
DKIM Signature in email with the private key
DKIM-Signature: v=1; a=rsa-sha1; c=relaxed/relaxed; s=fnc; d=env.etransmail.com; h=To:From:Reply-To:Subject:Message-ID:List-Unsubscribe:MIME-Version:Content-Type:Content-Transfer-Encoding:List-Unsubscribe:Date; bh =DEEFSFDSFWEEEfdfgdsgeERFSFMps774=; b=oDQdtCY85ckhjSDFSDFEdsfsdfdsfasedf9+sVkuMD5bpevJB4SB3+HEP0pikyDQpeLEWOeC2rwyrhDucDYctVYRr6DSFDFEdsfsdfdsfasedf9+s afasdfawessfF8DFEdsfsdfdsfasedf9+sVkuMD5bpevJB4SB3+HEP0pikyDQpeLEWOeC2rwyrhDucDYctVYRr6DSF
Working: While both DKIM and SPF involve the common step of adding a TXT record in DNS, DKIM implementation requires additional steps. Here's how DKIM works:
- Generate public and private keys: For DKIM, you need to generate a public key and a private key. The private key, which remains securely stored on your email server, is used to encrypt the email signature.
- Encrypt email signature: The private key is used to encrypt the email signature, which is then included as a header in every email sent from the server.
- Store public key hash in DNS: The hash of the public key is stored in a DNS TXT record. This key, along with the private key used for email signature encryption, is essential for email signature verification.
- Verify email signature: During email reception, the email receiving server verifies the DKIM signature. The values bh (Email signature), b (Encrypted key), and d (Signing domain) are examined and validated against the credentials in the DKIM TXT record within the email headers.
- Action upon validation: If the verification fails, the action taken depends on the email service's DKIM verification policy.
This is a sample of DKIM authentication results in Gmail.

DMARC
Structure:
_dmarc.mydomain.com. IN TXT "v=DMARC1\; p=none\; rua=mailto:[email protected]\; ruf=mailto:[email protected]\; pct=100"
Implementation:
Add DMARC record in the domain TXT record as shown below.
_dmarc.mydomain.com. IN TXT "v=DMARC1\; p=none\; rua=mailto:[email protected]\; ruf=mailto:[email protected]\; pct=100"
The parameters that are set in this code snippet have a specific function:
- p= DMARC Policy.
- v=Version.
- rua=Mailbox to which aggregate reports should be sent.
- ruf=Mailbox that will be receiving forensic reports.
- pct= Percentage of mail to which the domain owner would like to have its policy applied.
Here are a few policy parameters:
- p=none: In this policy setting, the email is treated in the same manner as it would be without any DMARC validation.
- p=quarantine: With this policy, the email is accepted but directed to a location other than the recipient's inbox, often placed in the spam folder.
- p=reject: This policy outright rejects the message, preventing it from being delivered to the recipient's inbox.
Working:
To implement a DMARC record, you must first establish SPF and DKIM records. Subsequently, DMARC settings are configured within the TXT records in your domain's DNS settings.
DMARC functions by achieving three primary objectives:
- Email authentication: It validates the authenticity of the email.
- Definition of actions for authentication failures: It specifies the actions to be taken when authentication fails.
- Enablement of reporting for domain spoofing: It enables the reporting of instances where a domain is being spoofed.
When an email is sent to the recipient's server, the DMARC record is checked for the parameters discussed earlier. DMARC conducts the following tests:
- Verification of the IP address in the SPF record.
- Validation of the DKIM signature.
- Domain alignment checks, including verifying that the messages’ "From" domain in the SPF record match its "return-path" domain.
Should the validation fail, actions are taken as defined in the DMARC policy, and a report is generated and sent to the respective email addresses specified in the DMARC record for reporting purposes.
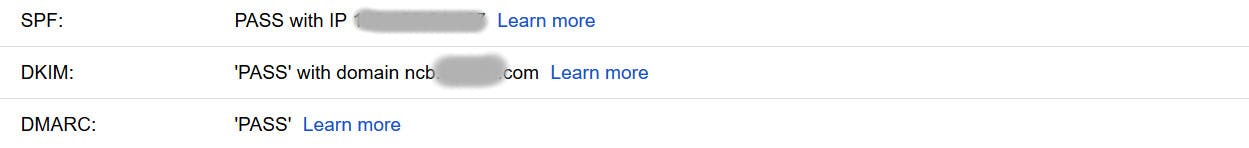
To confirm the validation status of SPF, DKIM, and DMARC for your received emails, you can review the original message, which provides detailed information about the email body and headers. In Gmail, you can access this information by selecting the "Show Original" option.
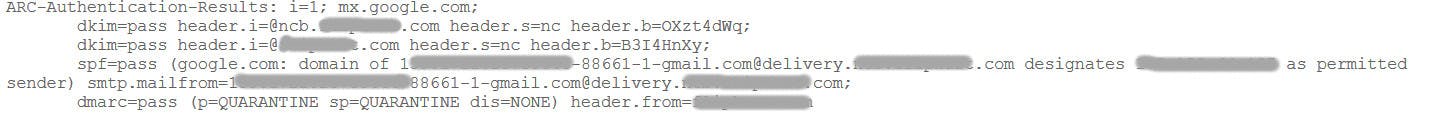
If you want to check the validation pass of the SPF DKIM and DMARC when you have received your emails is to see the original message to see the email body and headers in detail.
In Gmail you can do this by selecting the "Show Original" option.
At the top of the page now opened you will see the email Authentication passes.
ISP-specific support for email authentication
Not all ISPs provide support for each email validation. Here is a list of ISPs that offer support for SPF, DKIM, and DMARC, respectively.
Gmail
- SPF: Yes
- DKIM: Yes
- DMARC: Yes
Yahoo
- SPF: Yes
- DKIM: Yes
- DMARC: Yes
Outlook
- SPF: Yes
- DKIM: Yes
- DMARC: Yes
Zoho
- SPF: Yes
- DKIM: Yes
- DMARC: Yes
AOL Mail
- SPF: Yes
- DKIM: Yes
- DMARC: Yes
ISP Recommendations for Email Authentication
Gmail
Google strongly recommends using SPF, DKIM, and DMARC for email authentication within their system. By implementing all three email validation methods, your emails are considered more trustworthy by Gmail.
A failure in SPF alone won't immediately label you as spam or result in message rejection by the G-suite spam filter. However, if both SPF and DKIM validation fail, it could trigger Google to take action, such as marking your email as spam or dropping it.
When it comes to DKIM validation, Gmail has specific recommendations. To ensure your emails are DKIM-signed, it's advisable to use DKIM keys with a minimum length of 1024 bits. While using 512-bit signing won't lead to immediate rejection, it's not ideal for long-term usage, and it might cause issues.
Additionally, it's recommended to regularly rotate your DKIM encryption keys.
Google fully supports DMARC implementation and adheres to the DMARC credentials and policies defined by the user.
For more information on email validation within Google, please refer to this link.
New Gmail's guidelines (Effective February 1, 2024)
Gmail is enhancing security measures, particularly for high-volume senders. Effective February 1, 2024, if you send over 5,000 daily messages to Gmail accounts, adhere to the following requirements:
- Verify your email's identity with SPF or DKIM authentication.
- Maintain valid forward and reverse DNS records for sending domains or IPs.
- Keep spam rates under 0.3%, as per Postmaster tools.
- Format messages according to RFC 5322 standards.
- Implement DMARC email authentication for your sending domain.
- Avoid impersonating Gmail's From: headers to comply with DMARC quarantine policies.
- If regularly forwarding emails, include ARC headers in outgoing emails, and ensure mailing list senders include a List-id: header.
- Ensure alignment with SPF or DKIM domains for direct mail to pass DMARC alignment.
- Enable one-click unsubscribe with a visible link unsubscribe messages.
Take prompt and timely action if you send more than 5,000 emails daily to prevent potential email delivery issues.
Microsoft Outlook
Microsoft places a strong emphasis on SPF email validation, primarily relying on user ID-based verification through SPF credentials. t Individuals commonly encounter email delivery issues with Microsoft Outlook when SPF hasn't been properly configured.
To ensure trouble-free email delivery with Outlook, SPF validation is a must.
For 'onmicrosoft.com' domains, Microsoft 365 automatically establishes a DKIM setup. If your email addresses are under 'subdomain.onmicrosoft.com,' there's no need to configure DKIM.
If you choose not to configure DKIM, Microsoft 365 creates public and private keys and signs your emails using default DKIM settings.
In terms of DMARC records, Outlook is relatively accommodating. Even if your DMARC policy is set to reject emails, they won't be immediately discarded. Instead, they will be categorized as potential spoofed emails. You can then decide how to handle these emails. This gives you the opportunity to prevent legitimate emails from being rejected.
Microsoft recommends the implementation of all three validation methods: SPF, DKIM, and DMARC, for a comprehensive and effective email validation process within Microsoft Outlook.
If you are not sure how to implement email validation on Microsoft Outlook, you can check this link.
Yahoo
Yahoo permits SPF validation for a specific list of internal domains, which includes:
- yahoo.net
- yahoo.com
It's important to note that Yahoo has recently made a significant update to its default DMARC policy. They have set the policy to "p=reject" for emails originating from Yahoo domains. This means that any email sent from yahoo.com that doesn't come from Yahoo's own servers will be promptly rejected. This stricter DMARC policy is aimed at enhancing email security and reducing the chances of unauthorized emails using the yahoo.com domain.
For more help on Yahoo email authentication, check this link.
New Yahoo's guidelines (Effective February 1, 2024)
Yahoo, committed to delivering wanted messages and filtering out unwanted ones, introduces significant changes for bulk senders in the first quarter of 2024:
- Bulk senders should adopt robust authentication methods such as SPF, DKIM, and DMARC, following industry standards.
- They should facilitate one-click unsubscribes and respond to user requests within 48 hours.
- Maintain email content that aligns with users' preferences to keep their inboxes organized.
For a thorough assessment of your email program's authentication readiness, explore the tools available at EmailDojo.
AOL
AOL performs DKIM validation on incoming emails, using it as the primary authentication method to assess the reputation of IP addresses.
Furthermore, AOL scrutinizes DMARC records for inbound emails. Similar to Yahoo, AOL rejects emails that have undergone DMARC validation but failed to pass the validation process.
Zoho
Zoho exclusively supports the DKIM policy for emails generated from Zoho's servers and sent to external servers. Emails that are indirectly delivered to external servers or those not originating from Zoho's infrastructure are not supported or subjected to DKIM validation.
Some links for the Zoho mail configuration for email validation.
Conclusion
Conducting email validation on your messages is crucial for successful email delivery. It's essential to recognize that email policies will likely become more stringent in the future as a response to the growing number of email spoofing and breach attempts. When sending emails through specific ISP domains, take the time to review their validation policies on their website to gain a better understanding of how to optimize email deliveries.
If you are sending more than 5,000 emails in a day, remember to check and conform to the new guidelines from Gmail that will become effective from February 1, 2024.
We are a community of email enthusiasts. If you have further queries, feel free to drop an email to [email protected], and we would be happy to help you.
Excited about the latest in Bulk Email Marketing! Check out this insightful blog on Gmail and Yahoo updates in the email marketing landscape.
Explore the Blog - Here
Stay ahead of the game with valuable insights on optimizing your email campaigns! 📬
Grade My Email
Check your spam now?
Netcorecloud's toolkit is the solution to all your email problems.

You can also explore
Netcore connects & unifies your data across all sources, connects to your marketing channels and provides you with control over AI Powered automation and personalization.
Deploy emails that are
screenshot worthy!












Hitesh Pandey💻
Full Stack Developer, Pepipost
🥑 Developer Evangelist | 🥇Email Geek